Process of an Effective Transaction Monitoring Program
Process of an Effective Transaction Monitoring Program
Transaction monitoring is one of the most critical steps in the customer due diligence process, and it allows regulated entities to keep a check on suspicious transactions and mitigate money laundering and financial crimes.
However, to ensure that transaction monitoring is robust, an effective transaction monitoring program must be developed.
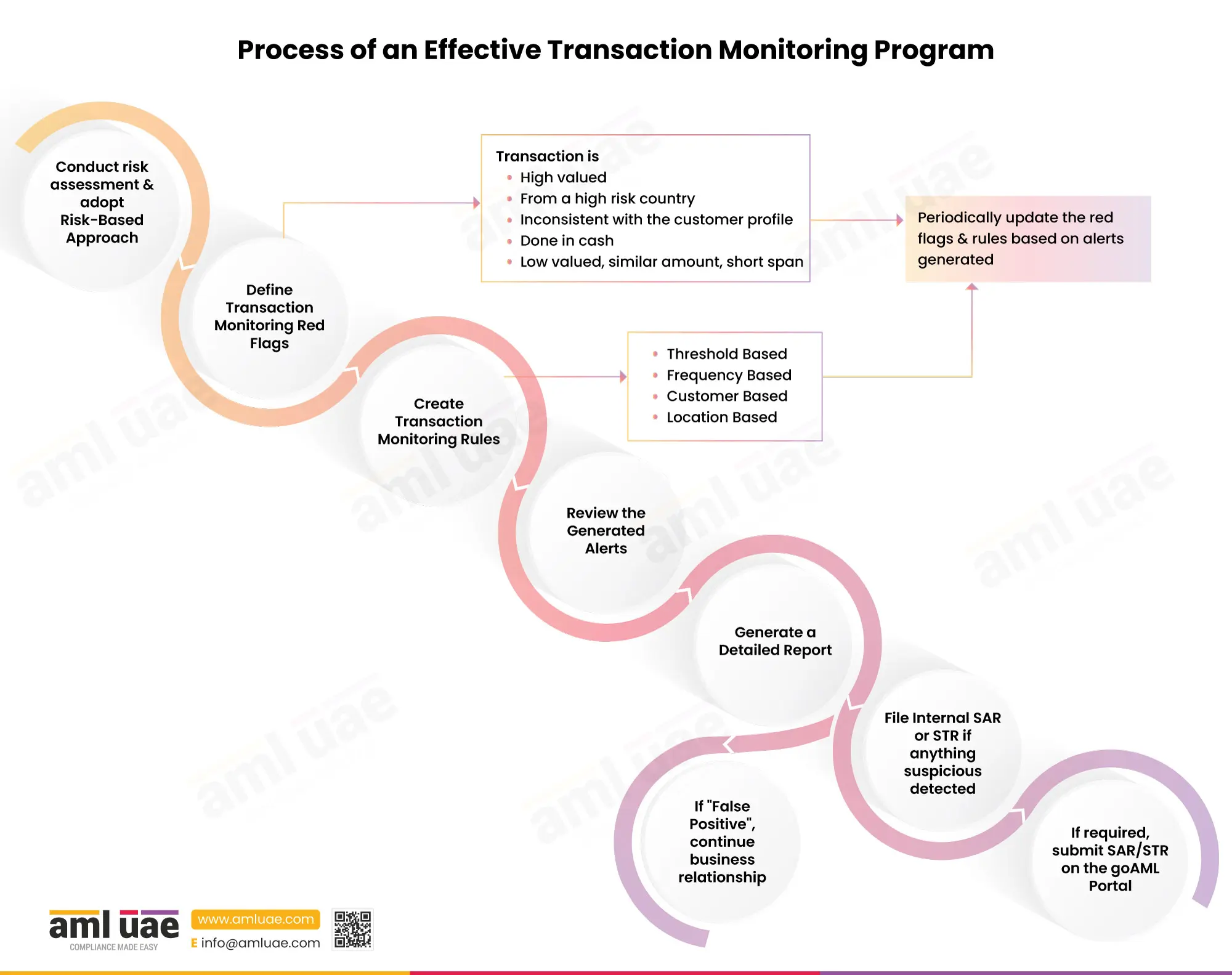
The first step in developing the program is conducting an enterprise-wide risk assessment to identify the risks regulated entities face from customers, products, and services and adopt the risk-based approach.
The second step is to define the transaction monitoring red flags. These red flags and risk indicators will help correctly identify suspicious transactions during ongoing monitoring. While defining these red flags, the business must consider the evolving trends and typologies associated with the industry in which it operates.
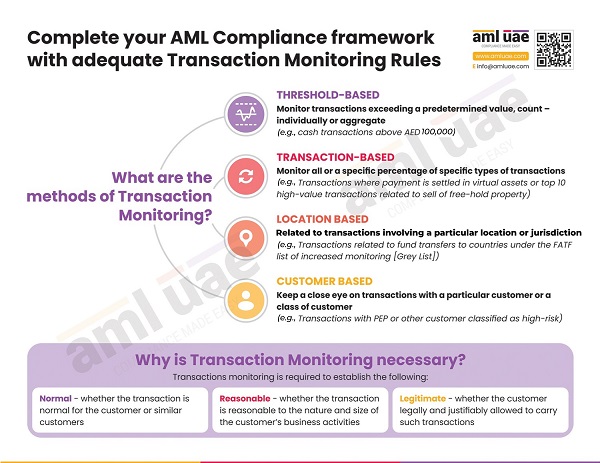
Based on the overall assessed risk and the identified red flags, the regulated entity needs to create transaction monitoring rules. The monitoring system will check the transactions against the defined rules. These rules must be validated and tested before the system is made live for ongoing monitoring.
If a transaction is carried out that doesn’t satisfy any of the rules, it will be marked suspicious, and an alert or warning should be triggered. The compliance team must check the alerts and generate a detailed report containing the nature of the alert, investigation requirements, customer risk classification, primary assessment of the nature of the risk indicator, etc.
In case of suspicion, the compliance team must file an internal Suspicious Transaction Report (STR), which the Compliance Officer will evaluate and perform an independent investigation, as may be required. Based on the review, the Compliance Officer shall report the suspicion on the goAML Portal or classify it as a “false positive” along with the reason.
The transaction monitoring rules and risk parameters must be periodically reviewed and updated to reduce the number of false alerts and identify suspicious activities in a timely manner.