A Complete Guide to ID Verification: Best Practices and Tools
What are ID documents?
Commonly known ID documents are government-issued identity documents such as passports, resident identity cards or driving licenses, among many such Identity (ID) documents, varying in terminology according to the jurisdiction where the authority is located.
For example- a government-issued identity document is commonly called an Aadhaar Card in India, an Emirates ID in UAE, a Pinyin Card in China, a National Identity Card (NIC) in Europe and a Social Security Number (SSN) in the USA to name a few.
What is ID verification?
Identity verification or ID verification is a process wherein the identity of the person they claim to be is verified against the document purported to be officially issued by the government or semi-government authority that such an individual presents to support such claim.
In simple words, ID verification is a security measure deployed to confirm the authenticity of an individual’s identity and the validity of a document supporting the identity claimed by such an individual.
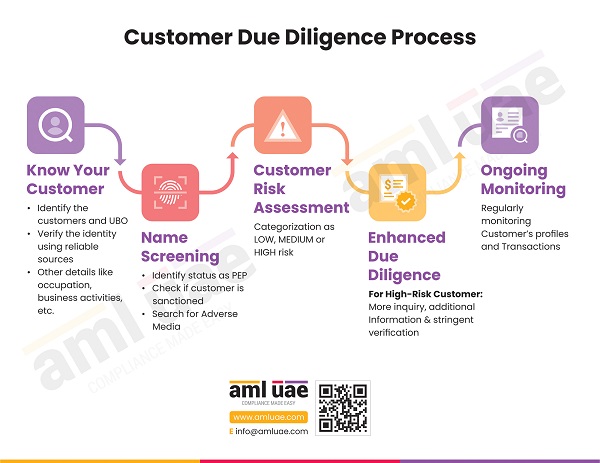
The ID verification process has become one of the routinely sought requirements for the Customer Due Diligence (CDD) process across various sectors such as Banking and Finance, Designated Non-Financial Businesses and Professions (DNFBPs), IT Services, healthcare, real estate, Virtual Assets activities and services, and many other sectors.
What is Digital Identity Verification?
The Digital Identity Verification is aimed at confirming an online identity. It uses various methods, such as biometric verification and facial recognition, to authenticate that the person is the one he claims to be.
What Are the Common Methods of Identity Verification?
Commonly used methods of identity verification include:
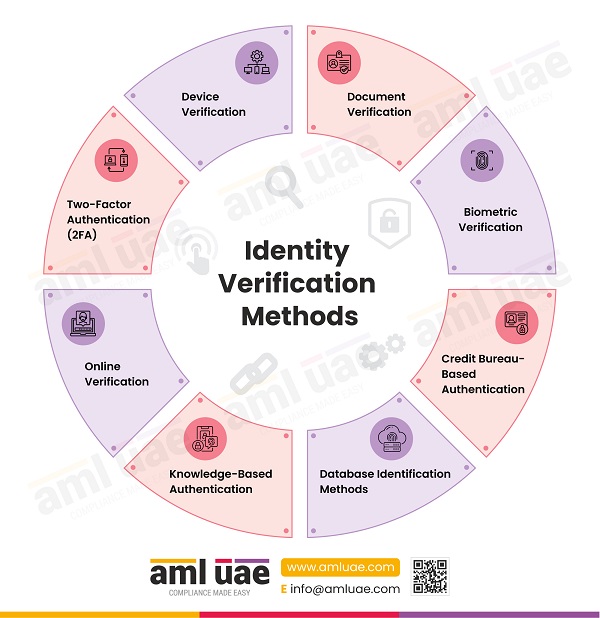
Document Verification
Document verification is the most common method to verify a person’s identity. The ID document is verified by examining its security features and details.
Biometric Verification
Using biometric information such as facial recognition, voice recognition, iris and retina scanning, and fingerprint matching with a database to confirm a match with the actual ID holder.
Credit Bureau-Based Authentication
This method relies on information from various credit bureaus, which hold vast credit information repositories on consumers, such as their names, addresses, and ID numbers.
Database Identification Methods
Database ID methods collect information from multiple sources to confirm a person’s identity. These sources include various social media platforms, including offline databases.
Knowledge-Based Authentication
Knowledge-based authentication (KBA) validates a person’s identity by prompting them to answer security questions specific and unique to that individual, which can be answered only by the person in question and not anyone else within a specified timeframe.
Online Verification
The online verification process includes determining whether a government-issued ID belongs to the person claiming it. Further, it includes using biometrics, AI, and human review. This method usually performs validity checks by prompting the person to share a selfie to ensure that the person holding the ID (during ID Verification) is the same person shown in the ID photo.
Two-Factor Authentication [2FA]
2FA includes two steps. As the name suggests, it requires the person to provide personal identification called a token and this token is requested to be provided when prompted for the same. Some of its examples are signing into a Google account using prompts provided on the registered email ID/device and phone number and entering the token to the login page from where it originated, in addition to entering the password.
Device Verification
The device verification method checks for the device’s legitimacy used to conduct a transaction.
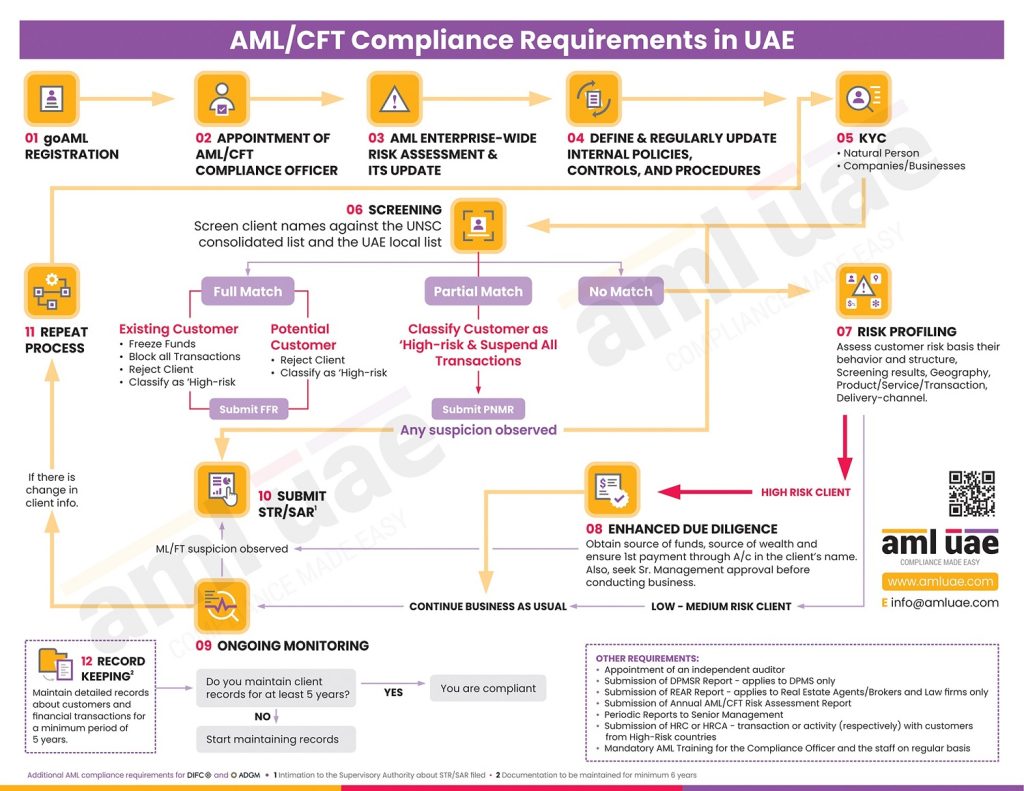
The Identify Verification Process
The ID verification process covers numerous stages aimed at confirming and validating a person’s identity, and these stages differ from business to business depending on their unique individual requirements. The infographic provides the usual flow of the ID verification process.
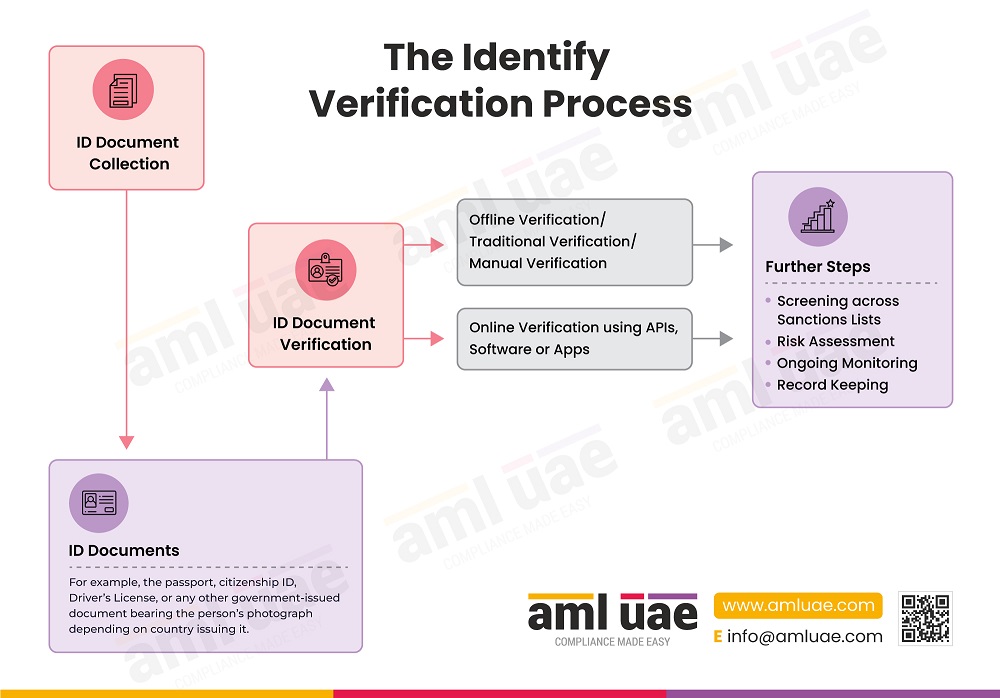
To sum it up, the ID verification process entails.
- Assessing ID verification needs
- Determine, implement, test, and revise the right ID verification method – whether offline/online, whether API to be used.
- Inform Customers and request for documents.
- Receive, verify, and validate ID documents.
Further steps include screening, risk assessment, ongoing monitoring, and record keeping.
Why is digital identity verification necessary?
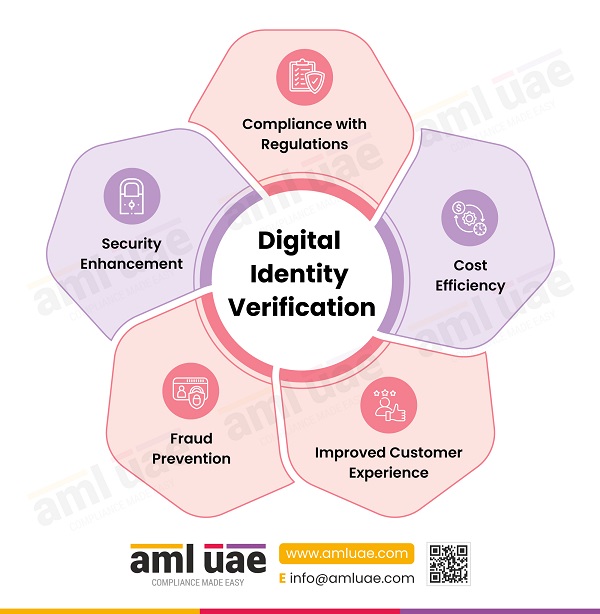
Compliance with Regulations
Anti-Money Laundering and Countering Financing of Terrorism (AML/CFT) Laws worldwide and recommendations of the Financial Action Task Force (FATF) call for identity verification as a requisite to prevent money laundering and terror financing (ML/TF). Thus, implementing identity verification programs helps businesses comply with AML/CFT laws.
Digital ID verification ensures that ID verification checks and balances are uniformly applied across the organization, records can be extracted whenever needed, and API integration with the government/regulator database ensures up-to-date compliance.
Cost Efficiency
Digital ID verification is undeniably more cost-efficient than manual ID verification as it brings down operational costs because most of its process is automated, and the verification process that requires intricate scrutiny is digitized, thus reducing human efforts significantly and bringing down operational costs.
Improved Customer Experience
Customer experience derived from Digital ID verification methods such as self-service login and filling of questionnaires, quick verification through QR code scanning at kiosks/counter-tops saves the customer from waiting in long queues and providing remote access to fulfil formalities instantly, thus ensuring customer satisfaction retention and low rates of abandonment.
Fraud Prevention
The very purpose of ID verification is to prevent financial crime in its initial stage by successfully identifying whether the person whose identity is being verified is an authentic person or not. Fraud can enter the organization through identity theft, online scams, account hacking, identity cloning, etc. By verifying an individual’s identity, fraud risk can be significantly prevented.
Security Enhancement
Confirming and validating individuals’ identities before entering business relationships ensures that only authorized individuals can access services and sensitive information, thus reducing the risk of data breaches and cyber-attacks.
Digital ID Verification Software Features
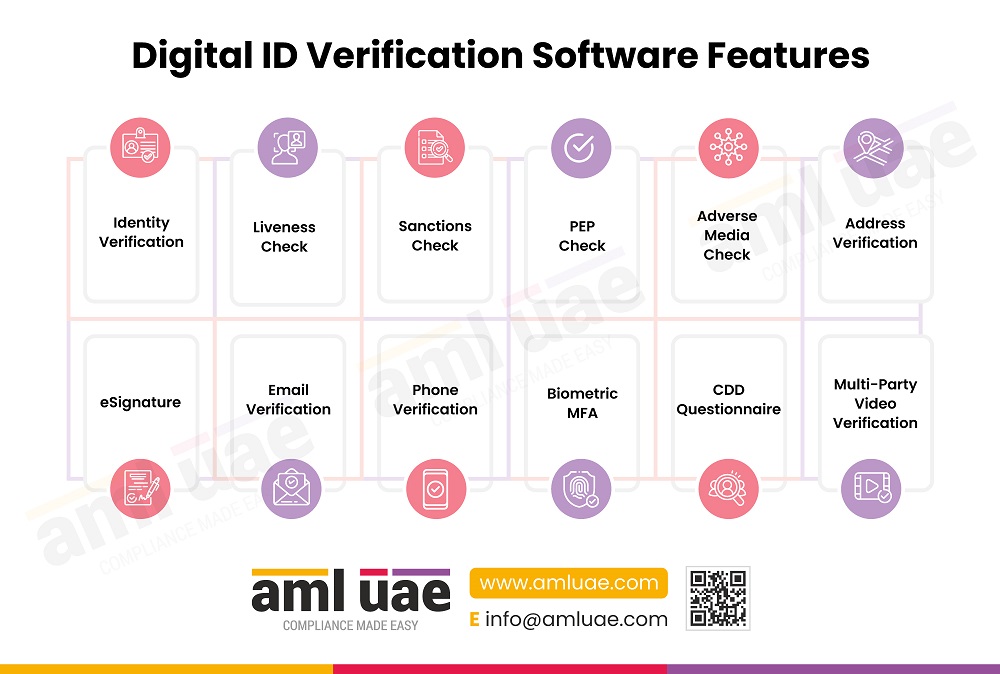
Identity Verification
Digital ID Verification Software helps verify government-issued IDs and performs biometric selfie matches.
Liveness Check
Liveness Check ensures the genuineness of the ID holder using a selfie video. One can also add various prompts to make this process more robust.
Sanctions Check
The underlying software performs sanctions checks against the UNSC and local sanctions lists as per the regulatory requirements and helps identify full, partial, or false matches.
PEP Check
The Screening Software comes with a global Politically Exposed Persons (PEPs) database and helps identify high-risk customers.
Adverse Media Check
The Digital ID Verification Software also comes with a feature where one can perform adverse media checks and identify risks associated with a customer.
Address Verification
The Digital ID Verification Sofware supports Optical Character Recognition (OCR) and saves valuable time. It validates proof of address documents like utility bills, bank statements, property lease agreements, etc.
Multi-Party Video Verification
Multi-Party Video Verification facilitates collective confirmation of the KYC information. It helps eliminate the risk of impersonation or fraudulent activities.
Customer Due Diligence (CDD) Questionnaire
One can customize the KYC form and add customer due diligence questions as per the regulatory requirements and risks associated with an individual.
Biometric MFA
Biometric MFA adds an extra layer of protection, making it difficult for unauthorized individuals to forge authentication, and it mitigates the risk of impersonation.
Phone Verification
Phone Verification helps perform Two-Factor Authentication.
Email Verification
Email Verification helps perform Two-Factor Authentication.
eSignatures
eSignature helps perform seamless customer onboarding and ensures legal compliance.
What is an Online ID Verification Service?
Online ID verification services are those that compare the identity a person claims to possess with data that proves it; these are identity proofing solutions which usually confirm/verify and validate government documents such as the passport, driver’s license, resident identity card, etc. with the person providing the same or claiming the same to be their ID.
Online ID verification services use APIs as discussed above to balance customer experience and security and help enterprises conduct business in a fast, efficient, safe, and compliant manner by preventing the imposition of penalties for non-compliance with AML/CFT, KYC and sanctions regulations – laws which call for robust identity verification.
Traditional Identity Verification vs. Digital ID Verification API
The pitfalls of the Traditional ID verification process entail
- Customer abandonment: The traditional ID verification process is elaborate and time-consuming and leads to incidences of onboarding abandonment while seeking to enrol with other companies that use API-based digital ID verification, which is much easier, faster, and grants a world-class customer onboarding experience.
- High Cost: The cost of ID document collection, scanning and verification is relatively high, especially when done in large quantities.
Digital ID verification by using an API has numerous benefits, such as
- Eliminating the need to re-verify customers who are previously or already registered.
- There is no need to verify and cross-check documents physically.
- Reduction in operational costs while using digital ID verification API as it provides a high return on investment.
- Improved end-customer experiences and increased onboarding success.
Thus, shifting to Digital ID Verification API is highly beneficial as it is secure, accurate and scalable for businesses with different needs.
How Can Technology Maximize the Effectiveness of Identity Verification?
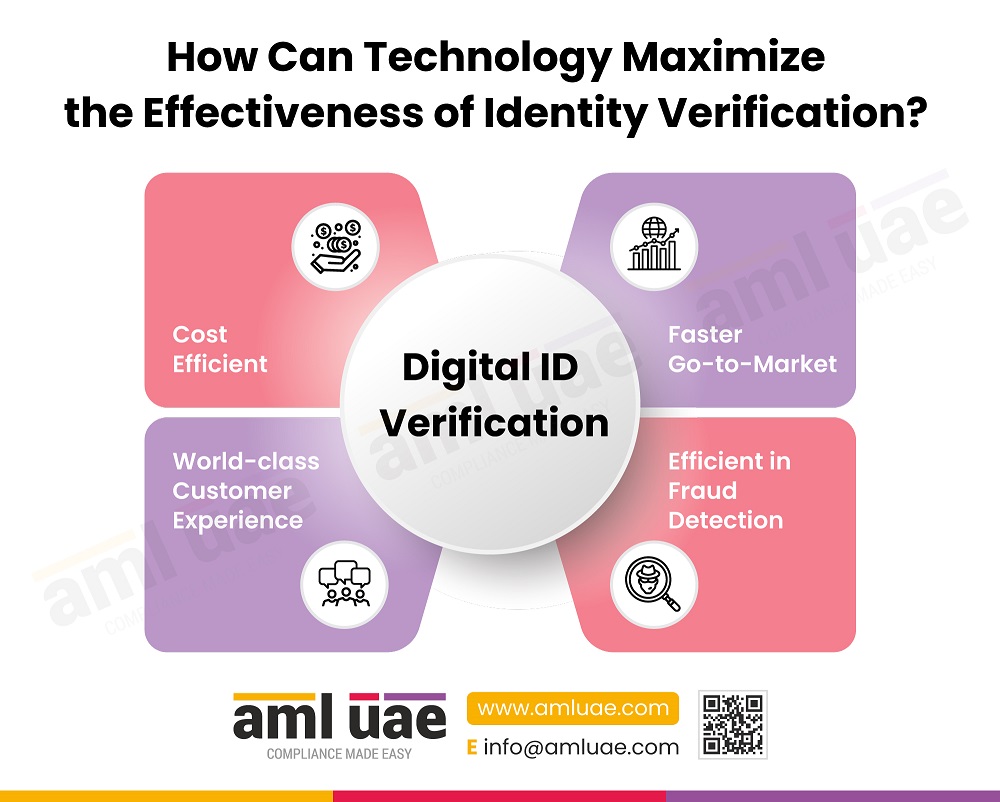
Shifting from the traditional method of collecting ID verification documents to the utilization of technology is essential in this age as it’s necessary to keep up with the advancement of technology.
It is only logical that organizations optimize the use of their resources by implementing fast, efficient, reliable, highly accurate, and compliant methods that can be used remotely and in real-time.
Digital Identity verification processes consist of a combination of biometric, AI-driven end-to-end feature sets powering workflows from ID capture and verification to proof of address and AML screening.
In simple words, the use of technology Increases the effectiveness of the ID verification process:
- Lowers the operational costs
- Reduces infrastructure costs while entering new markets without the need for a physical presence
- Increases the chances of fraud detection, thereby lowering the compliance cost
- Increasing customer satisfaction, thus lowering abandonment rate by having fully remote and almost instant access through mobile apps.
How to Choose the Right ID Verification API
Due to stringent regulatory requirements, such as customer due diligence, ID verification has become a mandatory process for businesses when onboarding individuals to prevent fraudulent activities and AML/CFT violations. The ID verification Application Programming Interfaces (API) are tools that enable efficient ID verification for the same.
What is an API and how it works?
API is a software intermediary that allows two applications/software to communicate using a set of protocols. A simple daily use example is the Weather Department’s software system, which contains daily data and updates of the status of weather reports, and the ‘weather app’ on our cell phones communicates (using API) with weather department software and provides us with real-time information on weather updates.

A similar example from the AML/CFT perspective would be the Sanctions and Targeted Financial Sanctions lists maintained by the United Nations Security Council Resolution (UNSCR), Office of Foreign Assets Control (OFAC), etc., that are accessed by various ID Verification and Sanctions Screening APIs to give results across the name of individual/businesses screened for compliance purposes.
Selecting the suitable ID Verification API
- ID verification API should be easy to embed into the onboarding workflow, enabling quick and efficient ID verification that is compliant with local and international AML/CFT laws
- API should be able to carry out an age verification process for several age-restricted products and services such as online gaming, online dating, online gambling, etc.
- API should be able to capture IDs through OCR and extract ID information.
- API should be able to verify the authenticity of the information captured from supposed ID documents provided by the customer
- API should be able to validate ID document numbers such as passport number, driver’s license number, Social Security numbers (SSNs), Emirate ID number (EID), etc., across the document provided to validate the same.
- API should verify the phone numbers provided by customers
- API should be ideally ISO certified GDPR compliant and should provide options such as
- direct integration
- Integration Via Core Providers
- Integration Via 3rd Parties
- API should provide a unified solution for AML/CFT compliance, client onboarding and client self-service for the customer due diligence process.
- The API provider should ideally provide sufficient development support, tutorials, cloud SaaS, usage tier-based pricing, and on-premise integration.
- The API should be white-labelable to suit businesses’ branding and privacy requirements.
- Ultimately, the API should
- Lower Operational Costs
- Lower Infrastructure Costs
- Lower Compliance Costs
- Lower Fraud Rate
- Lower Abandonment Rate
- Thus giving a Return on Investment that is sizeable in nature.
How Does Identity Verification Weave Its Magic Across Different Sectors?
The need for digital ID verification is no longer limited to the banking or finance sector. Its scope has widened to curb illegal activities and ensure compliance with regulations imposed by authorities. Sectors that require ID verification to conduct their business in a safe and compliant manner are:

Banking and Finance
Due to the inherently risky nature of business, the banking and finance sector is most prone to fraud. It requires digital ID verification to comply with regulations such as AML/CFT laws and KYC requirements.
Digital ID verification helps automate compliance with citizenship and sanction regulations. KYC needs are fulfilled through AI data extraction and validation from the provided Proof of Address documents.
Regulatory compliance is ensured through global regulations that involve validation of customer ID, addresses and information for AML/CFT and KYC compliance.
Designated Non-Financial Businesses and Professions (DNFBPs)
DNFBPs comprise a wide range of entities and individuals involved with activities outside the scope of the traditional financial sector. Still, they can be exploited for ML/FT purposes or other illicit financial activities.
The Financial Action Task Force/FATF prescribe DNFBPs to combat ML/FT as they are vulnerable and responsible for identifying and mitigating risks associated with financial crimes. Broad categories of DNFBPs include:
Lawyers, Notaries, Conveyancers, and Other Independent Legal Professional
Legal professionals such as lawyers and notaries provide legal services, including property conveyancing, trust creation, and company formation.
Accountants, Auditors, and Tax Advisors
Accountants, auditors, and tax advisors are responsible for maintaining financial records, conducting audits, and guiding individuals and businesses on tax matters.
Real Estate Agents, Developers, and Brokers
Professionals in the real estate industry, including agents, developers, and brokers, facilitate property transactions, such as buying, selling, and leasing real estate properties.
Dealers in Precious Metals, Jewels, and Stones
This category encompasses businesses engaged in buying, selling, or trading precious metals like gold and silver and dealing with jewellery and valuable gemstones.
Trusts and Company Service Providers
These entities specialize in creating, managing, and administering trusts, companies, or other legal structures for clients.
Casinos, Online Gaming, and Gambling Establishments
Casinos, online gaming platforms, and gambling establishments fall into this category, as they handle financial transactions related to gambling activities
Insurance Firms, Agents, and Brokers
Insurance companies, agents, and brokers are involved in selling and providing insurance products and services.
Virtual Asset Service Providers (VASPs)
Entities involved in cryptocurrency trading, exchange platforms, and virtual currency wallet services.
The abovementioned sectors have to implement an ID verification process and record keeping as a part of their AML/CFT compliance framework to maintain the integrity of the economic system.
ID verification is the first step for the mandatory customer due diligence (CDD) process, following which risk assessment, enhanced due diligence and ongoing monitoring of business relationships are conducted.
Age Restrictive Sectors
Alcohol, Dating Services, Online Gambling, Online Gaming
They fall under the restricted goods category globally and require compliance with age-restriction law provisions. Age Verification APIs can provide quick and efficient age validation tools.
What Are the Legal and Regulatory Requirements for Identity Verification?
Compliance with global ID verification regulations is essential for businesses while collecting, handling, and using personal information.
Non-compliance with regulations could lead to imposition of fines and penalties and loss of reputation. Awareness of and compliance with ID verification regulations can help businesses detect and prevent non-compliance with regulations and prevent events such as identity theft, account hacking and other fraud.
A few general ID verification regulations include:
AML/CFT Regulations
AML/CFT laws across the globe include but are not limited to:
- Federal Decree-Law No. (20) of 2018 On Anti-Money Laundering and Combating the Financing of Terrorism and Financing of Illegal Organisations applicable in the UAE.
- Guidance for Licensed Financial Institutions on Digital Identification for Customer Due Diligence issued by the Central Bank of the UAE.
- Anti-Money Laundering Directives (AMLD) and Sixth Anti-Money Laundering Directive (6AMLD) by the European Union
- Money Laundering, Terrorist Financing and Transfer of Funds Act 2017, the Proceed of Crime Act 2002, and the Terrorism Act 2000 are applicable in the UK.
- Federal Act on Combating Money Laundering and Terrorist Financing in the Financial Sector 1997, also referred to as the Anti-Money Laundering Act (AMLA), is applicable in Switzerland.
- The Bank Secrecy Act (BSA), the Patriot Act, and the Anti-Money Laundering Act 2020 (AMLA) are applicable in the USA.
- The Monetary Authority of Singapore (MAS) provides AML/CFT supervision in Singapore.
- Financial Transaction Reports Act 1988, the Anti-Money Laundering and Counter-Terrorism Financing Act 2006 and the Australian Transaction Reports and Analysis Centre (AUSTRAC) provide AML/CFT supervision in Australia.
- Prevention of Money-Laundering Act, 2002, applicable in India.
United Nations Security Council Resolutions
UNSCR mandates its member states to implement measures to prevent terrorism, including identity verification, sanctions screening, and business relationship monitoring requirements for regulated businesses.
Financial Action Task Force (FATF) Recommendations
FATF 40 recommendations are applicable globally, and these provide guidance on AML/CFT measures, including customer due diligence and identity verification requirements to be implemented while applying Risk Based Approach (RBA) to mitigate the risk that business is exposed to from their potential customers, further, the risk is prioritized according to attributes the customer risk poses such as demographic, age distribution, homogeneity, market size etc.
These regulations prevent criminals from using established financial systems and businesses for ML/FT and require regulated institutions to verify the identities of their customers.
Data Protection and Data Privacy Laws
Compliance with global regulations encompassing the rights of an individual and their rights over the use of their data by the data controller and data processer, to name a few; data protection regimes across the globe include but are not limited to
- The Personal Data Protection Law, UAE, Federal Decree-Law No. 45 of 2021, regarding the Protection of Personal Data
- General Data Protection Regulation (EU GDPR)
- California Consumer Privacy Act (CCPA)
- The California Privacy Rights Act of 2020
- Digital Personal Data Protection (DPDP) Act, 2023, India
- The Personal Data Protection Act (PDPA), Singapore
Know Your Customer KYC Regulations/Requirements
KYC regulations usually originate from AML/CFT and FATF recommendations and require regulated businesses to identify and verify the identity of their customers to prevent money laundering, fraud, and terrorist financing.
Electronic Identification, Authentication and Trust Services (eIDAS) regulation
This EU-based regulation provides a legal framework for electronic identification and trust services, including digital signatures, seals, and timestamps.
Payment Card Industry Data Security Standard (PCI DSS)
This global standard applies to businesses that accept credit card payments and includes requirements for identity verification to prevent fraud.
Electronic Signatures in Global and National Commerce Act (ESIGN)
It is a US law providing a legal framework for electronic signatures and verification recognized globally.
Red Flags Associated with Digital Identity Verification
- Concealment of true Identity or Lack of valid identity proof
- PO box or phone number associated with an answering service or is a foreign national with no significant dealings in the country and apparent economic or other rationale for doing business with the business/organization conducting verification.
- Concealment of Beneficial ownership (for corporate clients).
- Fund sources.
- Transaction reasons.
- Inconsistent or Altered Documents
- Documents that appear fake, altered, or otherwise inauthentic.
- Inconsistent identity document numbers
- Suspicious or inconsistent personal information (such as a wrong address on a document)
- Personal information is inconsistent across multiple sources.
- Personal information is associated with known fraud activity and cases.
- An existing customer is unable to answer challenge questions correctly.
What Are the Challenges and Risks Associated with Identity Verification?
Challenges faced with the ID verification process include:
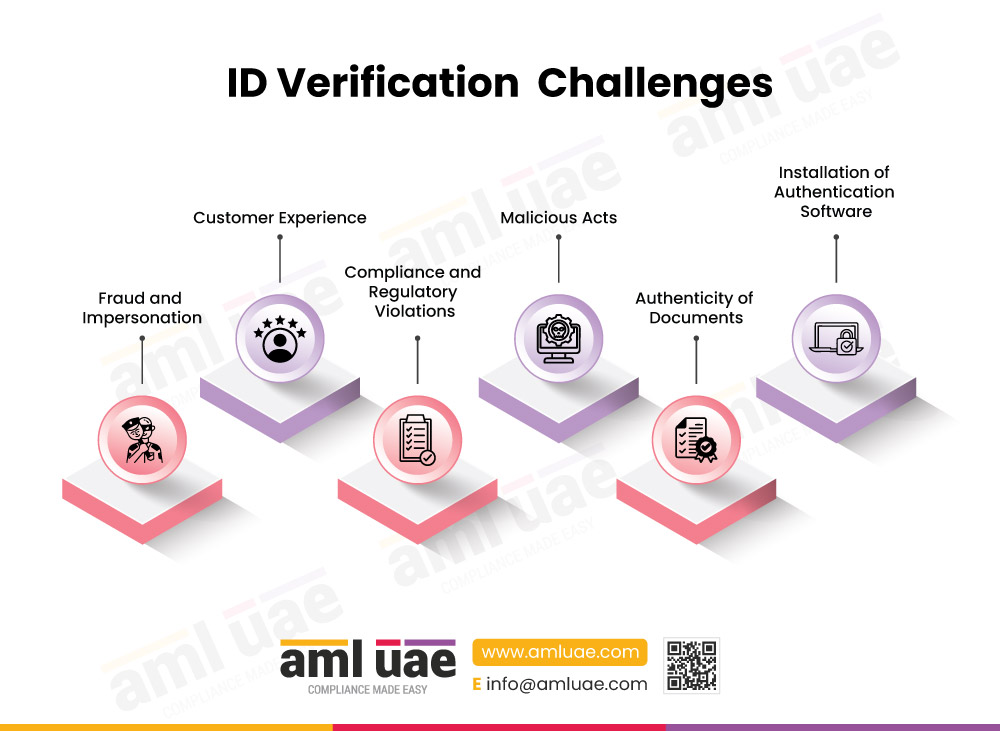
Fraud and Impersonation
After establishing a business relationship, it is natural for businesses to exchange sensitive information with their counterparties. Fraudsters and Identity thieves create fake accounts and impersonate legitimate users to gain access to confidential information. It leads to violation of the Data Protection and Privacy rights of individuals.
Customer Experience
Manual ID verification processes are paper-based and time-consuming. Businesses need to strike a balance between customer experience and compliance requirements. Digital ID Verification solutions provide a world-class experience and security while handling the customer onboarding processes.
Malicious Acts - Identity Theft and Fraud
Using stolen private data or creating fake identities to gain unauthorized access harms the business reputation, leads to loss of customers, and brings down customer trust.
Authenticity of Documents
Authenticating the validity of identity documents is a necessary step in the verification method. Coming across fake identities, whether modified or forged, out of the documents that are hard to distinguish from the original, while document cross-verification may lead to false positives against ID verification checks. This makes it essential for businesses to install advanced document verification techniques.
Installation of Authentication Software
Incorporating identity verification tools such as APIs into existing applications can be complicated if not taken care of, especially for large-scale businesses with diverse systems and platforms. Ensuring a smooth integration process without disrupting existing systems is essential.
What Are the Best Practices for Identity Verification?
By implementing best practices, businesses can ensure compliance with identity verification requirements prescribed in AML/CFT regulations across the globe and protect their customers’ personal information from identity fraud and other illicit activities.
Some of the suggestive best practices include:
Adoption of Risk Based Approach (RBA)
Implementing and formulating ID verification measures commensurate with the risk the business is exposed to is important as not all ID verification APIs or programs are the same and constantly evolve to meet business needs. By using RBA, businesses can customize the ID verification process to the level of risk it is exposed to for a particular client or transaction.
AML/CFT Compliance Framework
A formally drafted and approved Compliance Framework can help businesses ensure that they adhere to all relevant identity verification, AML/CFT, data protection and data privacy regulations.
The compliance framework should include policies and procedures for collecting, retaining, and using personal information for future use, as well as processes for monitoring and reporting any violations of regulations, such as suspicious activity reports.
Data Encryption and Security
Implementing data encryption protocols and cybersecurity measures through a reliable ID verification API solution that safeguards sensitive user information from breaches.
Obtaining Explicit Consent
Obtaining explicit consent from customers is a legal requirement prescribed by various global data protection and data privacy regulations for collecting and using their personal information. Businesses should ensure that customers know what information is being collected and how it will be used and obtain their consent before verifying.
Customer Behaviour Observation
APIs that can assess odd user behaviour in real-time and respond quickly to any security threat.
Global Compliance Regulatory Standards
Ensure that the business is equipped with the latest fraud-detecting techniques. Also, ensure that the ID verification and authentication methods align with regional compliance standards to minimize legal risks.
Multi-Factor Authentication (MFA) Implementation
Implementing MFA ensures that an extra layer of security is provided to customers. This could include something customers already know (password), device access (a mobile device/laptop/PC), and biometric data.
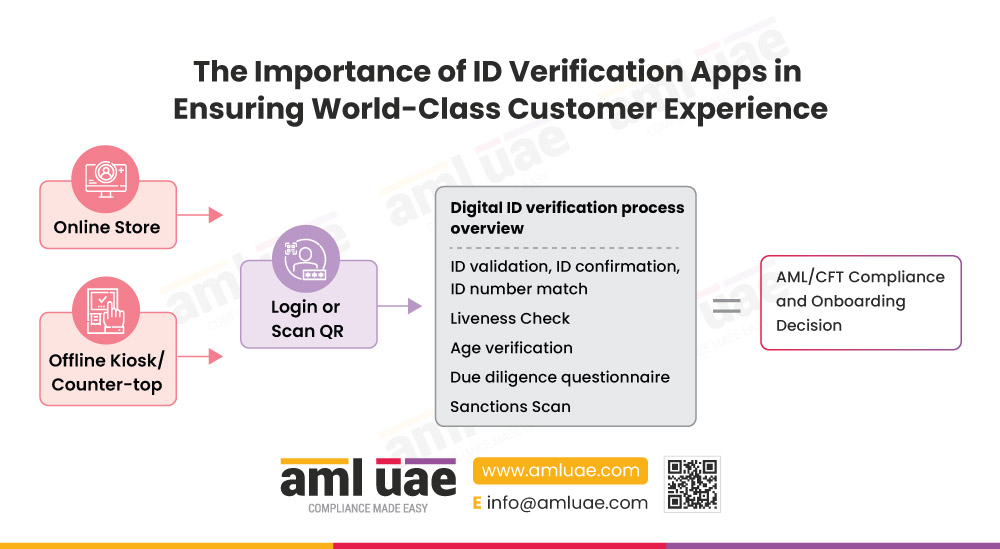
The Importance of ID Verification Apps in Ensuring World-Class Customer Experience
An ideal ID verification App ensures World-Class Customer Experience by facilitating the end-customer with
- Global coverage supporting ID types from all over the world, ensuring seamless accessibility.
- Accurate verification of good customers against fraud by keeping fraud attempts negligible, thus reducing inherent risk.
- Multi-factor authentication – adding biometric authentication that enhances security, data protection and customer experience.
- Password reset and account recovery through self-service solutions.
- Enable real-time, multi-party transactions through live video verification that is remotely accessible
- Provide for eSignatures feature wherever required to ensure the legality of electronic contracts and agreements.
- Automated verification of the identity of customers to avoid duplication of efforts.
- Ability to detect and incorporate NFC chip damage into adaptive process flow, reducing the requirement of asking for fresh IDs in case of damaged IDs.
- Enabling self-verification through self-service on their device through QR codes or kiosks by filling out Customer Due Diligence questions and activating their accounts for said service.
What Future Trends and Innovations Illuminate Identity Verification's Path?
As the saying goes, “Necessity is the mother of all inventions.” The same holds true for any innovation that comes into being; the very need to innovate or improvise arises from a lack of accessible and practical solutions to problems encountered by the public at large. Such issues and their future ‘fixes’ – which are innovations and future trends, include:
Liveness Check and Proof of Humanity:
When it comes to ensuring the genuine presence of an individual whilst conducting online/remote Identity verification using a video call, ‘Liveness check’ detects if the subject is a real live human or a bot. It provides an additional layer of security to ensure that the user is a real and unique person, thus enhancing the value of online platforms.
Digital Avatars:
Digital IDs (DIDs)or Digital Avatars are created on open-source, public blockchains, are unique, and can be independently controlled by the individual, thus eliminating the need to depend on third parties for identity verification.
The Digital Avatar will complete the KYC/ID verification procedures, such as verifying the identity of any person seeking to create an account, maintaining records of the information used to verify the person’s identity and ultimately determining whether the person appears on any government-provided lists of known or suspected terrorists or terrorist organizations.
Centralized ID:
The need for centralized ID is the most pressing one. Think of the current situation; most of us have at least one bank account, but the minute we decide to open a second one, we must go through all formalities, such as the elaborate and time-consuming ID verification process. Having a centralized framework will eliminate the need for repeated ID verification processes.
Fraud reduction:
Future IDs will undoubtedly have features or attributes that would be near impossible to forge, steal or mimic, which shall play a significant role in cancelling out the events of identity theft.
Conclusion
ID verification is essential to ensure compliance with AML/CFT laws. Digital ID verification is the need of the hour, and companies would experience smooth customer onboarding and significant time and cost savings by implementing it.
AML UAE provides end-to-end consulting services to help you identify the right Digital ID Verification software, assess and analyze associated risks, and suggestive solutions to ensure world-class customer experience while balancing AML/CFT compliance requirements.
In AML/CFT compliance, customer identification and verification are crucial. The right AML software allows complying with the rules and regulations efficiently. It helps to build customer trust and promote business growth. AML UAE is a popular and reliable AML consultant that offers a comprehensive range of AML compliance services.
Make significant progress in your fight against financial crimes,
With the best consulting support from AML UAE.
Our recent blogs
Share via :
About the Author
Pathik Shah
FCA, CAMS, CISA, CS, DISA (ICAI), FAFP (ICAI)
Pathik is a Chartered Accountant with more than 22 years of experience in compliance management, Anti-Money Laundering, tax consultancy, risk management, accounting, system audits, IT consultancy, and digital marketing.
He has extensive knowledge of local and international Anti-Money Laundering rules and regulations. He helps companies with end-to-end AML compliance services, from understanding the AML business-specific risk to implementing the robust AML Compliance framework.
Identity Verification FAQs
ID verification is an exercise where the ID document of a person is verified against the person claiming it to be theirs.
We need to perform ID verification to
- ensure compliance with laws and regulations and avoid fines, penalties
- identifying fraudulent activity by ensuring transparency, security, and privacy
- ensure that a natural person is behind the transaction, not a bot or AI-driven tool.
- avoid money laundering and terror financing concerns
- bring down the inherent risk of onboarding new customers to the business
The ID verification process, in brief, consists of
- Seeking ID document from the customer to verify.
- Receive ID document.
- Compare, verify, and validate ID document.
The Anti-Money Laundering KYC regulations include the authentication of customers, ID verification, address verification, biometric verification, and face verification. Regulations also require identification and periodic updating of customer’s sensitive and personal information.
Businesses can benefit from Digital ID verification by speeding up the customer onboarding process by –
- Improving customer experience and ensuring a seamless onboarding experience and rates.
- Avoid non-compliance.
- Identifying fraudulent accounts and transactions.
- Incorporating an efficient and cost-effective AML compliance program.
